DNS hijacking and spoofing
DNS is the underlying directory framework of the Internet. It turns a web address into an IP address that ultimately directs the user to legitimate website. If this DNS gets hijacked or taken over by a hacker group, the web address can be redirected to a completely different website. This malicious website may contain the phishing content or malware. Once the user has been directed to this malicious website the user is exploited by the criminal. So in case no social engineering has been used to trick the user. The criminal has only used technical capabilities or launch and execute their attack.
Since DNS spoofing is a technical attack you can protect against it with technical solutions such as Domain Name system monitoring and Anti-Pharming services. Using https also protects against DNS spoofing since the attacker does not has the certificate for the requested name. None of these things help against phishing, since this attack is not against a technical based trust system but against a social trust system.
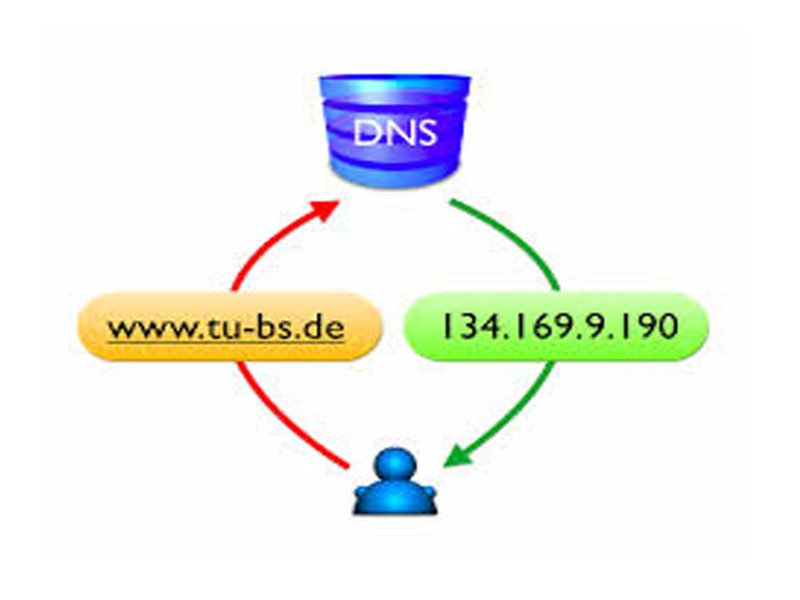
DNS Hijacking, Spoofing and Pharming are phishing type relate fraud techniques. DNS hijacking or spoofing is a cybercrime attack that re-routes web traffic to a malicious web site. The attacker hijacks or infects the DNS query to insert an incorrect result to re-direct the web traffic unbeknown to the user. The user has entered the correct domain/URL into the browser but they end up on a fake website.
Phishing uses a both technical techniques and social engineering to drive the unsuspecting user to a malicious website, whereas, DNS hijacking uses just technical methods to re-route web traffic.
We have covered popular phishing methods previous in this blog. Usually the social engineering involves an email or message to trick gullible users into visiting the fake site. The phishing site looks like and feel like a trusted site, such as a banking site.

